Rule Set Privileges Management
In this section:
Applications
To disable an item, highlight the item, right-click and select Change State. This toggles between disable and enable. This can be useful when needing to trouble shoot with Support.
- Select the Privilege Management node for a rule set.
- Right-click and select Application > File.
The Add a File for User Privilege Management dialog displays. - In the Properties tab, click the ellipsis (...) in the text box:
- In the Open dialog, navigate to the file that you want to add and click OK.
- Substitute environment variables where possible
- Use regular expression
- Make file an Allowed Item. If selected you can also select to allow the file to run even if it is not owned by a trusted owner.
- Enter optional command line arguments in the Arguments text box. Enter all arguments as they appear in Process Explorer.
- Command line arguments extend the matching criteria beyond what is entered in the File field. If an argument is added, both file and argument must be satisfied for a match to occur. Any argument that appears on the command line for a process, such as flags, switches, files, and Guids, can be added.
If required, you can select the following:
|
Denied File |
Allowed File |
Result |
|---|---|---|
|
shutdown.exe |
shutdown.exe Arguments: -r -t 30 |
shutdown.exe runs only when -r -t 30 is on the command line - anything else run by shutdown.exe is denied. |
To configure the arguments of an allowed or denied item correctly, they must appear as they do in Process Explorer for example:
File: C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE
Command line: "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\example.docx
Would be configured as:
File: Absolute or relative path of winword.exe
Arguments: /n C:\example.docx
- To apply a policy, select the policy from the drop-down in the Policy section.
- You can select the following options for the policy:
- Apply to child processes
- Apply to common dialogs
- Install as a trusted owner
- If required, enter an optional description of the file for your future reference.
- To add metadata to the file, select the Metadata tab:
- To automatically complete the fields select Populate metadata from file.
- Click Add to add the file to the rule set.
The file item is added to the Applications view on the Privilege Management work area.
The following fields can be populated: Product Name, Vendor, Company Name, File Description, File Version, and Product Version.
You can refine any of the data; select the required check box and edit the fields.
If Vendor metadata is enabled, a further option becomes available - Verify certificate at runtime. When this option is enabled, the agent verifies the certificate whilst it is matching the file. Click Verify Options to access a further set of criteria, used during file matching.
For further information, see Verify Options.
- Select the Privilege Management node for a rule set.
- Right-click and select Application > Folder.
The Add a Folder for User Privilege Management dialog displays. - In the Properties tab, click the ellipsis (...) in the text box:
- In the Open dialog, navigate to the folder that you want to add and click OK.
- Substitute environment variables where possible
- Include subfolders
- Use regular expression
- Make folder an Allowed Item. If selected you can also select to allow the files to run even if it is not owned by a trusted owner.
- To apply a policy, select the policy from the drop-down in the Policy section.
- You can select the following options for the policy:
- Apply to child processes
- Apply to common dialogs
- Install as a trusted owner
- If required, enter an optional description of the folder for your future reference.
- To add metadata to the folder, select the Metadata tab:
- To automatically complete the fields select Populate metadata from file.
- Click Add to add the folder to the rule set.
The folder item is added to the Application view in the Privilege Management work area.
If required, you can select the following:
The following fields can be populated: Product Name, Vendor, Company Name, File Description, File Version, and Product Version.
You can refine any of the data; select the required check box and edit the fields.
If Vendor metadata is enabled, a further option becomes available - Verify certificate at runtime. When this option is enabled, the agent verifies the certificate whilst it is matching the file. Click Verify Options to access a further set of criteria, used during file matching.
For further information, see Verify Options.
Enables you to specify a new file hash to which the selected policy will be applied. For detailed information on adding a file hash.
- Select the Privilege Management node for a rule set.
- Right-click and select Application > File Hash.
The Add a File Hash for User Privilege Management dialog displays. - In the Properties tab, click the ellipsis (...) in the text box:
- In the Open dialog, navigate to the file hash that you want to add and click OK.
- Make file hash an Allowed Item. Select to add the file hash to the Allowed Items list.
- Enter optional command line arguments in the Arguments text box. Enter all arguments as they appear in Process Explorer.
- Command line arguments extend the matching criteria beyond what is entered in the File field. If an argument is added, both file and argument must be satisfied for a match to occur. Any argument that appears on the command line for a process, such as flags, switches, files, and Guids, can be added.
- To apply a policy, select the policy from the drop-down in the Policy section.
- You can select the following options for the policy:
- Apply to child processes
- Apply to common dialogs
- Install as a trusted owner
- If required, enter an optional description of the file hash for your future reference.
- The file hash value is displayed, select Rescan to update the file hash.
- Click Add to add the file hash to the rule set.
The file hash item is added to the Application view in the Privilege Management work area.
- Select the Privilege Management node for a rule set.
- Right-click and select Application > Rule Collection.
The Rule Collection Selection dialog displays. - Select the Add to Rule check box for the collection(s) that you want to the rule set.
- Once you select a collection you can specify the following settings:
- Make Allowed - select to make the rule collection an allowed item.
- Allow Untrusted Owner - If Make Allowed is selected, you can select to allow the files to run even if it is not owned by a trusted owner.
- Apply to Child Processes - Select to apply settings to all child processes.
- Apply to Common Dialogs - Select to apply settings to common dialogs.
- Install as Trusted Owner - Select to install as a Trusted Owner.
- Click OK to add the collection(s) to the Applications view in the Privilege Management work area.
Components
Add Component Displays the Select Components dialog.
Filter the view by supported operating system and select the name of the control panel and management snap-in component(s) you want to add to the rule.
Self-Elevation
Enable Self-Elevation - Select to enable self elevation and apply the required setting:
- Only apply Self-Elevation to items in the list below
- Apply Self-Elevation to all items except those in the list below
Options - Displays the Self-Elevation Options dialog.
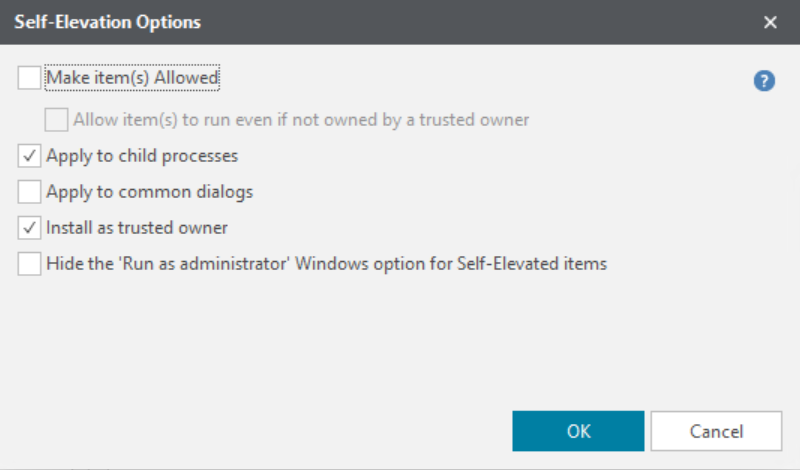
Self-Elevation Options
| Option | Description |
|---|---|
| Make Item(s) Allowed | Make the rule items allowed and overwrite any associated allowed items. |
| Allow items to run even if it is not owned by a trusted owner |
This option is available when Make item(s) Allowed is selected. When selected, all the rule items listed are executed regardless of the owner. |
| Apply to child processes | By default, the Self-Elevation Policy applied to rule items is not inherited by child processes. Select this option to apply the policy to the direct children of the parent process. |
| Apply to common dialogs | Elevate access to the Open File and Save File Windows menu options when a file or folder has been elevated. By default, any common dialogs are not elevated. |
| Install as trusted owner | Make the local administrator the owner of all files created by the defined application. This option is not applied to regular applications, only installer packages. |
| Hide the 'Run as Administrator' Windows options for Self-Elevated items | Hide the Run as Administrator option from the Windows shortcut menu. |
- Select the Privilege Management node for a rule set.
- Right-click and select Self-Elevation > File.
The Add a File for Self-Elevation dialog displays. - In the Properties tab, click the ellipsis (...) in the text box:
- In the Open dialog, navigate to the file that you want to add and click OK.
- Substitute environment variables where possible
- Use regular expression
- If required, enter an optional description of the folder for your future reference.
- Select the Metadata tab.
- To automatically complete the fields select Populate metadata from file.
- Click Add to add the file to the rule set.
The file item is added to the Self-Elevation view on the Privilege Management work area.
If required, you can select the following:
The following fields can be populated: Product Name, Vendor, Company Name, File Description, File Version, and Product Version.
You can refine any of the data; select the required check box and edit the fields.
If Vendor metadata is enabled, a further option becomes available - Verify certificate at runtime. When this option is enabled, the agent verifies the certificate whilst it is matching the file. Click Verify Options to access a further set of criteria, used during file matching.
For further information, see Verify Options.
- Select the Privilege Management node for a rule set.
- Right-click and select Self-Elevation > Folder.
The Add a Folder for Self-Elevation dialog displays. - In the Properties tab, click the ellipsis (...) in the text box:
- In the Open dialog, navigate to the folder that you want to add and click OK.
- Substitute environment variables where possible
- Use regular expression
- Include subfolders
- If required, enter an optional description of the folder for your future reference.
- Select the Metadata tab.
- To automatically complete the fields select Populate metadata from file.
- Click Add to add the folder the rule set.
The folder item is added to the Self-Elevation view on the Privilege Management work area.
If required, you can select the following:
The following fields can be populated: Product Name, Vendor, Company Name, File Description, File Version, and Product Version.
You can refine any of the data; select the required check box and edit the fields.
If Vendor metadata is enabled, a further option becomes available - Verify certificate at runtime. When this option is enabled, the agent verifies the certificate whilst it is matching the file. Click Verify Options to access a further set of criteria, used during file matching.
For further information, see Verify Options.
- Select the Privilege Management node for a rule set.
- Right-click and select Self-Elevation > File Hash.
The Add a File Hash for Self-Elevation dialog displays. - In the Properties tab, click the ellipsis (...) in the text box:
- In the Open dialog, navigate to the file hash that you want to add and click OK.
- If required, enter an optional description of the file hash for your future reference.
- The file hash value is displayed, select Rescan to update the file hash.
- Click Add to add the file hash to the rule set.
The file hash item is added to the Self-Elevation view on the Privilege Management work area.
- Select the Privilege Management node for a rule set.
- Right-click and select Self-Elevation > Rule Collection.
The Rule Collection Selection dialog displays. All privilege management rule collections are listed. - Select the Add to Rule check box for the collection(s) that you want to the rule set.
- Click OK to add the collection(s) to the Applications view in the Privilege Management work area.
System Controls
Use System Controls to control the ability to perform any of the following actions. Controls can be applied to elevate or restrict access to the specified item.
- Uninstall Control Item: Use this option to allow or restrict installed applications from being uninstalled when the rule conditions have been matched. Uninstall Control Items are configured by defining which applications are controlled. Further validation can be applied to target a named publisher and specific application versions. To allow or restrict all applications from a publisher, enter a * in the Application field combined with the publisher name.
- Service Control Item: Use this option to select which services can be modified, stopped, started and restarted when the Rule conditions have been matched.
- Event Log Control Item: Use this option to select which event logs can or cannot be cleared when the Rule conditions have been matched. Event log control items are configured by selecting the name of the log or logs to be controlled.
- Process Termination Control Item: Use this option to protect processes, such as anti virus software, from termination by all users, including administrators. Users can still stop processes gracefully, for example, by clicking close in an application UI, but they cannot forcibly terminate a process, such as ending a task from the Details tab in Task Manager. An individual file can be specified or all processes in a particular folder can be targeted.
The Agent Service is the only service that cannot be restarted once stopped.
Service Control Items are configured by specifying the display name and/or the internal name. The service display name may differ between different localized Operating Systems, whereas the internal name will remain the same. Therefore, if this configuration will be used across different locales, it is recommended only the internal name is used.
Optionally, add Metadata to include additional criteria for matching files and folders.